Technology ❯Cybersecurity ❯Data Protection
Incident Response Hacking Techniques Access Control Data Breaches Hacking Password Security Data Leaks Software Development Criminal Technology Malicious Software Data Breach Response Risk Management Government IT Systems Secure Systems Intelligence Operations University Systems Threats to Data Intrusion Detection Threat Mitigation Digital Forensics Voting Data Cloud Storage Data Theft Corporate Surveillance

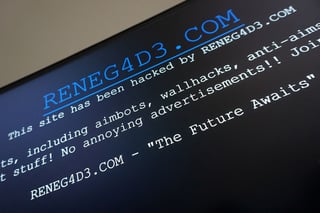
Restrictions include travel bans, fortnightly court appearances, passport surrender, designated residence, monitored communications under a sealed National Court probe led by Spain’s counterterrorism agencies.