Technology ❯Cybersecurity ❯Malware
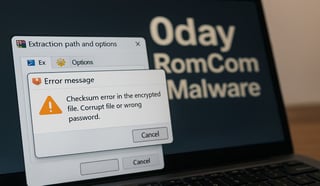
XZ-Utils Backdoor Reconnaissance Tools XZ Utils SparrowDoor SSH Backdoor Non-Volatile Memory NVRAM Backdoor OVERSTEP Remote Access Trojans Remote Code Execution RustyClaw ToolShell Overstep Linux

Talos researchers released an operational timeline with IoCs to guide organizations in securing exposed servers