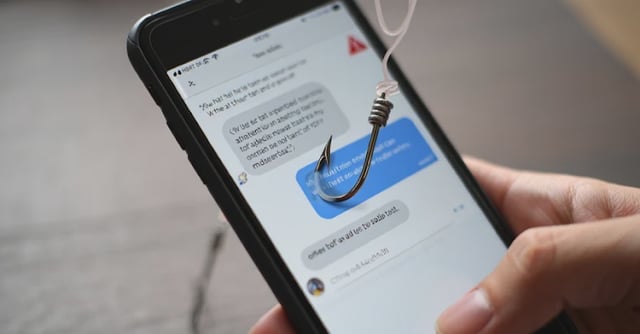
Overview
- SEKOIA traced ongoing phishing texts to Milesight industrial routers after honeypots captured suspicious requests on July 22, 2025.
- Researchers identified roughly 18,000–19,000 routers reachable online, with at least 572 exposing inbox and outbox APIs that allow unauthenticated SMS sending and retrieval.
- Targets concentrated in Belgium, Sweden and Italy, with typosquatted domains impersonating CSAM, eBox and major banking, postal and telecom brands.
- Logs show campaigns active since October 2023, with SEKOIA assessing exploitation as far back as February 2022 and finding no evidence of backdoors on the devices.
- Infrastructure frequently relied on NameSilo‑registered domains and Lithuanian host Podaon, with mobile‑only delivery, anti‑debug scripts and Telegram logging linked to a bot named GroozaBot.