Overview
- The disclosed exploit chain affects Unitree’s G1 and H1 humanoids as well as Go2 and B2 quadrupeds used in labs, universities, and some police departments.
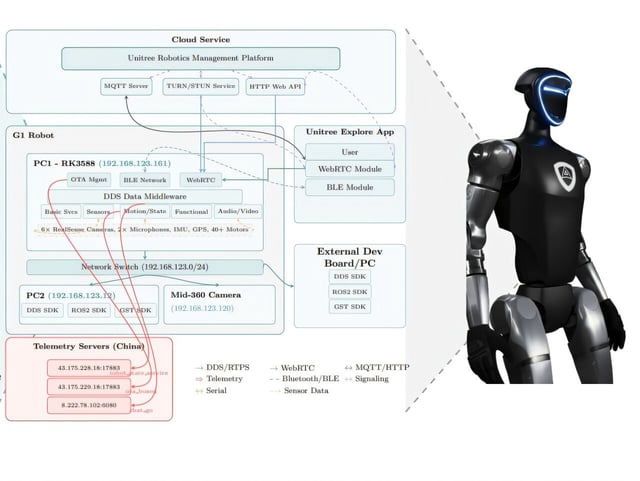
- Researchers detail a BLE-based Wi‑Fi onboarding weakness using hardcoded keys, a trivial "unitree" handshake, and unsanitized input leading to remote root command execution.
- Infected units can wirelessly compromise nearby Unitree robots, enabling a self-propagating botnet according to the public UniPwn release on September 20.
- An arXiv audit from Alias Robotics documents four CVEs and reports that the G1 sends telemetry to servers in China every five minutes without user notification.
- Unitree acknowledged the issues on September 29 and pledged near-term updates, while researchers advise disabling Bluetooth and onboarding via Wi‑Fi only until patches are verified.