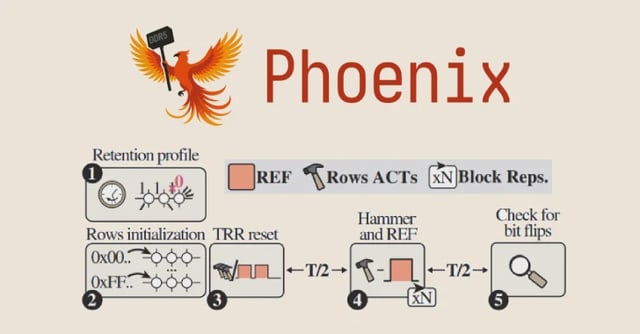
Overview
- Tracked as CVE-2025-6202, Phoenix reliably triggered bit flips on all 15 tested SK Hynix DDR5 DIMMs manufactured between 2021 and 2024.
- The team demonstrated a privilege-escalation exploit that obtained root on a commodity DDR5 system with default settings in as little as 109 seconds.
- The technique exploits unsampled refresh intervals and uses self-correcting synchronization to stay aligned with thousands of refresh operations.
- Tripling the DRAM refresh rate blocked the attack in tests at roughly an 8.4% performance cost with potential stability risks, prompting a push for per-row activation counting.
- Researchers from ETH Zurich and Google released a paper, PoC code and open-source FPGA test platforms after notifying vendors on June 6, and AMD has issued BIOS updates for some client systems.