Overview
- Tailored emails posing as legal copyright or IP complaints are hitting organizations across the U.S., Europe, the Baltics and APAC, often citing Facebook Page IDs and ownership details and sent from Gmail accounts.
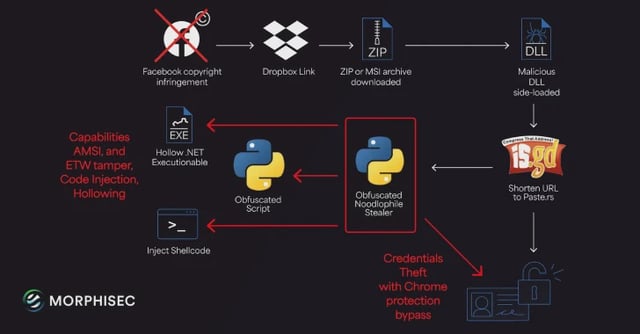
- The lure links to a Dropbox download that delivers a ZIP or MSI containing a signed app abused for DLL side-loading, with Haihaisoft PDF Reader cited as one of the legitimate binaries used.
- Malicious components are disguised as documents or images that unpack into BAT scripts and portable Python interpreters, which set persistence through Registry or Startup entries.
- An obfuscated staging layer pulls a resolver from Telegram group descriptions to fetch the final payload from paste[.]rs, with in-memory execution and LOLBin abuse used to evade disk-based defenses.
- The stealer harvests browser cookies, credentials, autofill data and saved cards, gathers system details, and self-deletes after execution, and its code includes placeholders suggesting future features like keylogging, screenshots and file encryption.