Overview
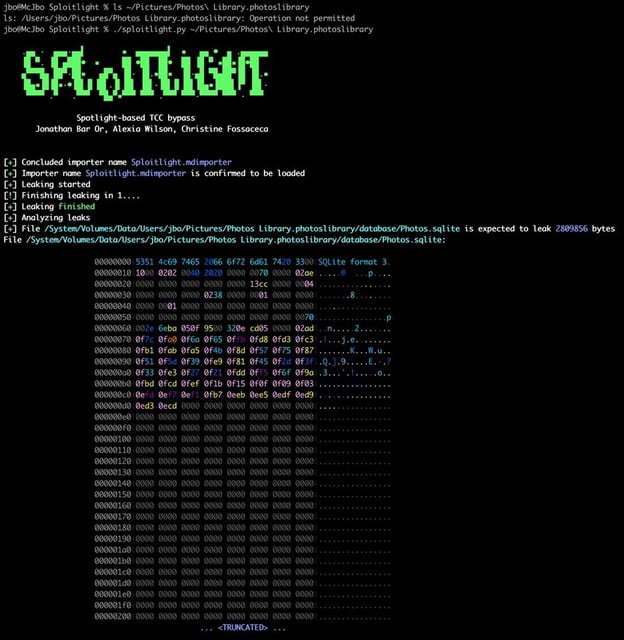
- Microsoft Threat Intelligence released a detailed report on July 28 showing how modified Spotlight importers could log and exfiltrate TCC-protected files without user consent.
- Apple closed the flaw tracked as CVE-2025-31199 in macOS Sequoia 15.4, iOS 18.4, and iPadOS 18.4 on March 31 by improving data redaction and tightening plugin validation.
- Sploitlight could have exposed precise geolocation, photo and video metadata, face recognition tags, AI-generated summaries, and user preferences across devices linked via iCloud.
- No signs of Sploitlight exploitation have been observed in the wild, as Apple’s swift coordinated disclosure and patch preceded the public reveal.
- Security tools now detect anomalous Spotlight plugin activity, and Microsoft recommends that all macOS, iOS, and iPadOS users ensure their systems run the latest updates.