Overview
- The group now relies on cloud features to exfiltrate data, destroy backups, and extort victims through compromised Microsoft Teams accounts without deploying traditional endpoint malware.
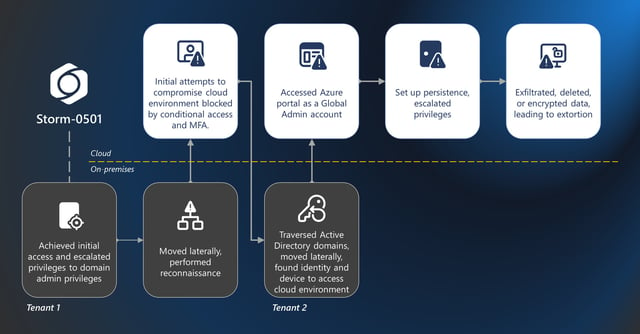
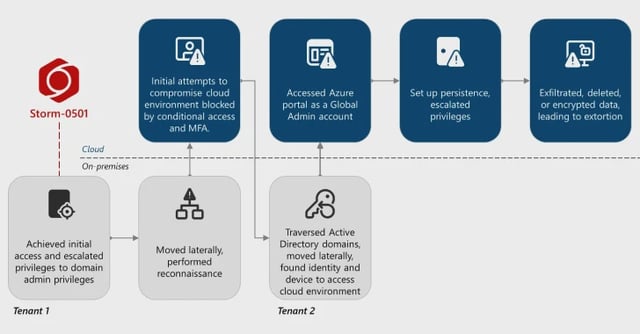
- In a recent large-enterprise breach, attackers used DCSync and compromised Entra Connect servers to locate a non-human Global Administrator without MFA, reset its password, register attacker-controlled MFA, and sign in to the Azure portal.
- They created persistence by registering a malicious federated tenant, abused Microsoft.Authorization/elevateAccess/action to obtain Owner roles, then exfiltrated data and mass-deleted Azure resources, in some cases re‑encrypting cloud data with new keys.
- Microsoft attributes the success of the intrusion to fragmented hybrid deployments with multiple Active Directory domains, separate Azure tenants, and inconsistent Defender coverage that left unmanaged devices and visibility gaps.
- Microsoft introduced an Entra ID change to block abuse of Directory Synchronization Accounts and released Entra Connect v2.5.3.0 with Modern Authentication, alongside guidance to enable TPM on sync servers, enforce MFA, and apply least-privilege and backup controls.