Overview
- Microsoft’s Digital Crimes Unit acted under a Southern District of New York order with Cloudflare and the U.S. Secret Service to dismantle RaccoonO365 infrastructure and block re‑registration on Cloudflare.
- Microsoft identified Joshua Ogundipe of Nigeria as the alleged leader of the operation and submitted a criminal referral to international law enforcement.
- The phishing kits were sold by subscription via a private Telegram channel with more than 850 members, priced from $335 for 30 days to $999 for 90 days, generating at least $100,000 in cryptocurrency since July 2024.
- Campaigns using the service stole more than 5,000 Microsoft credentials across 94 countries, including a tax‑themed wave that targeted over 2,300 U.S. organizations and activity against at least 20 American health care entities.
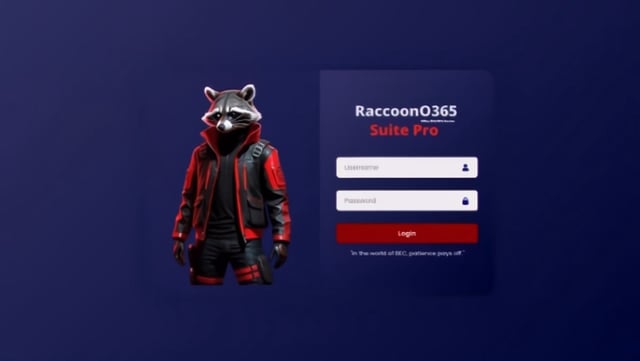
- RaccoonO365 spoofed Microsoft 365 login pages, captured session cookies to bypass multifactor authentication, featured anti‑analysis and evasion code, and enabled up to 9,000 phishing emails per day, which investigators say may have facilitated hundreds of millions of messages.