Overview
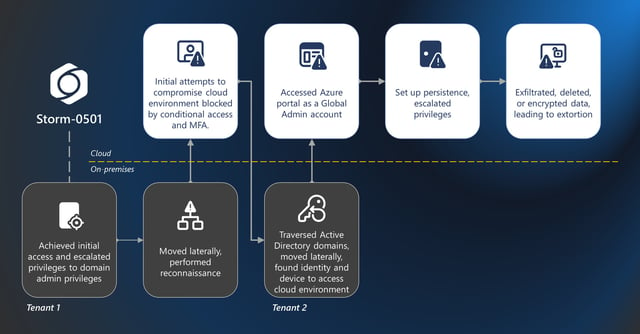
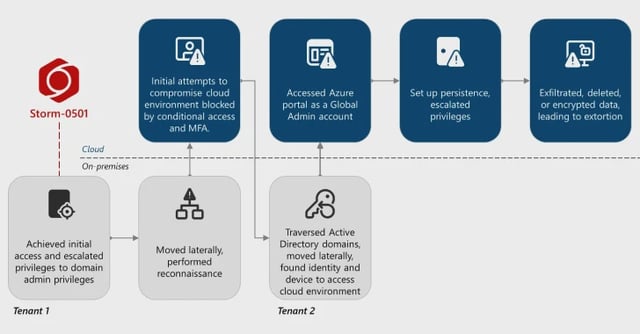
- Microsoft says Storm-0501 broke into a large enterprise’s on-premises and Azure environments, exfiltrated and destroyed data, then demanded payment via a compromised Microsoft Teams account.
- The intruders compromised Entra Connect Sync servers, ran DCSync to obtain credentials, found a synced non‑human Global Administrator without MFA, reset its on‑prem password, and registered attacker-controlled MFA to reach the Azure portal.
- With Global Admin access, the group elevated privileges to roles such as Azure Owner and User Access Administrator, registered an attacker tenant as a trusted federated domain, and forged SAML tokens for persistent impersonation.
- Researchers attribute the breach’s success to fragmented identity and security coverage across multiple AD domains and Azure tenants, noting inconsistent Microsoft Defender deployment created critical blind spots.
- Microsoft published mitigations and Entra ID changes to curb Directory Synchronization abuse, urging TPM on sync servers, universal MFA, conditional access, least privilege, and unified visibility across hybrid environments.