Overview
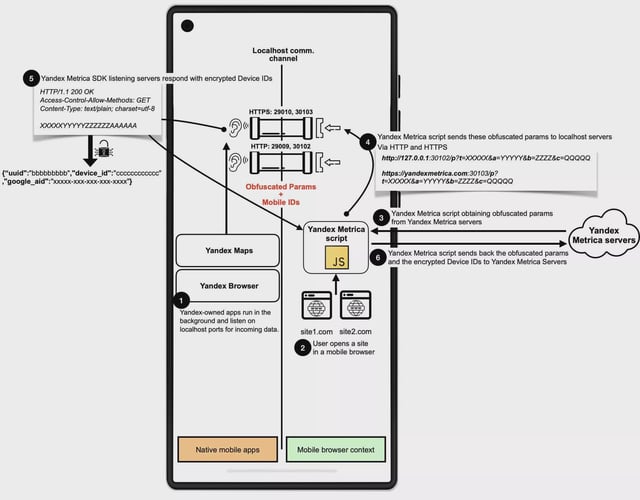
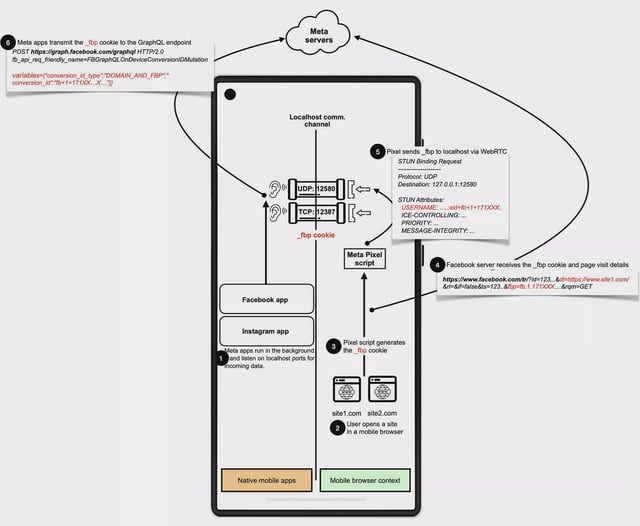
- An international team from IMDEA Networks, Radboud University and KU Leuven found that Android apps like Facebook, Instagram and Yandex’s Maps and Browser silently listened on fixed local ports to capture browser cookies and metadata.
- The exploit bypassed Android’s permission controls and browser safeguards—including Incognito Mode and cookie clearing—by embedding JavaScript scripts that opened communication channels with native apps.
- Meta Pixel and Yandex Metrica, embedded on roughly 5.8 million and 3 million websites respectively, enabled the companies to track detailed user actions such as page views, searches, cart additions and purchases.
- Meta disabled the localhost-tracking feature on June 3 and is in discussions with Google to address policy concerns as Chrome, Firefox and DuckDuckGo deploy targeted mitigations.
- Google confirmed the practice violated its security and privacy principles, browser vendors are rolling out fixes, and regulators in jurisdictions like the EU may investigate potential breaches.