Overview
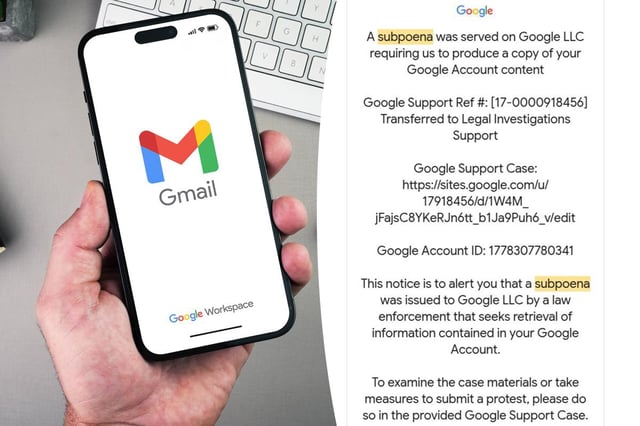
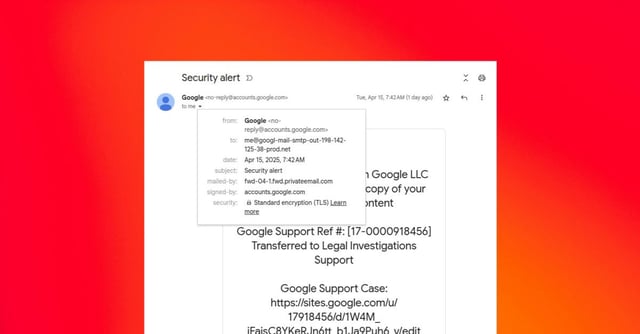
- A phishing campaign exploits Google's DKIM signing and Sites platform to send emails that appear to come from 'no-reply@google.com,' bypassing authentication checks.
- Scammers use fake subpoena alerts to trick recipients into entering credentials on fraudulent login pages hosted on sites.google.com.
- Google has rolled out interim protections to mitigate the vulnerability and is developing a permanent fix while urging users to enable two-factor authentication and passkeys.
- The phishing method was first reported on April 16 by Ethereum Name Service developer Nick Johnson, who nearly fell victim to the scam.
- A similar DKIM relay attack previously targeted PayPal users, emphasizing the growing sophistication of phishing tactics leveraging trusted platforms.