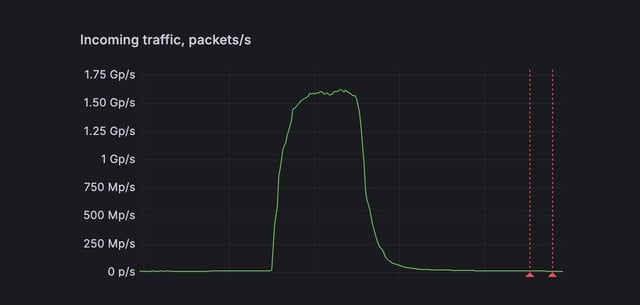
Overview
- FastNetMon says it detected the UDP flood in real time and used the customer's scrubbing infrastructure, including ACLs on edge routers, to prevent a major outage.
- The target, described as a DDoS scrubbing provider in Western Europe, was not named by FastNetMon.
- Malicious traffic came from compromised CPE, including IoT devices and MikroTik routers, distributed across more than 11,000 networks worldwide.
- A FastNetMon spokesperson told The Register the company observed a near-identical ~1.49 Gpps attack on an Eastern European scrubbing vendor that included an extortion email, suggesting the same botnet may be involved.
- The disclosure follows Cloudflare's report of mitigating an 11.5 Tbps assault peaking at 5.1 Bpps, underscoring escalating DDoS scale across bandwidth and packet-rate fronts as FastNetMon urges ISP-level filtering.