Overview
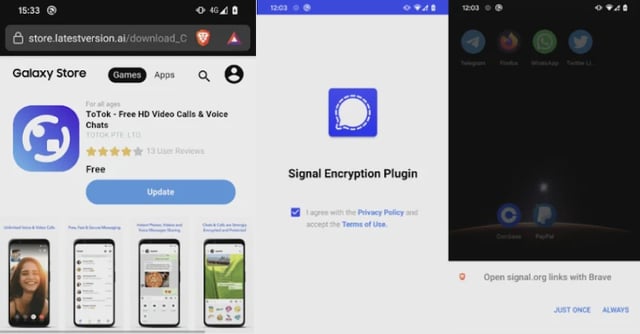
- ESET reports that the spyware was never available in official stores and was installed by victims from third‑party sites posing as trusted services.
- ProSpy masquerades as a non-existent Signal Encryption Plugin or a ToTok Pro upgrade, with activity believed to date to 2024 and discovery in June 2025.
- ToSpy impersonates the ToTok app via fake store pages, remains operational based on live command‑and‑control servers, and likely began around mid‑2022.
- Both malware families maintain persistence with foreground services, AlarmManager restarts, and auto‑launch on reboot while harvesting contacts, SMS, device details, media, documents, and chat backups.
- Deception techniques include mimicking the Samsung Galaxy Store, using a Google Play Services icon, and redirecting users to legitimate download pages, with detections concentrated in the UAE and attribution still unknown.