Overview
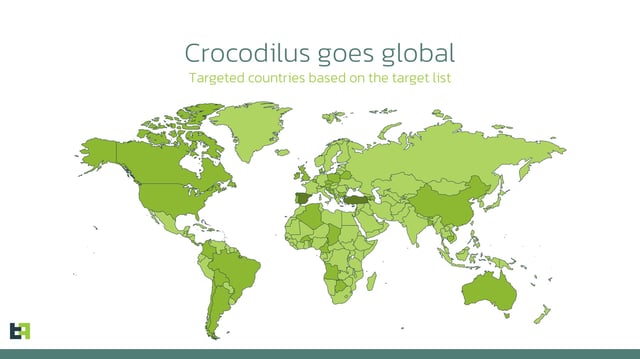
- Threat Fabric first documented Crocodilus in late March targeting Turkey and now reports victims across all continents as of June 2025.
- The malware uses Android’s ContentProvider API to add fake contacts that display trusted names instead of caller IDs during incoming calls.
- Injected entries remain local and unsynced with Google accounts to evade fraud prevention and appear genuine on infected devices.
- Crocodilus spreads through malicious apps promoted outside the Play Store—often via social media ads—and employs code packing and XOR encryption to slip past defenses.
- Security experts urge Android users to stick to official app stores, minimize unnecessary installations and keep Google Play Protect enabled to reduce risk.