Overview
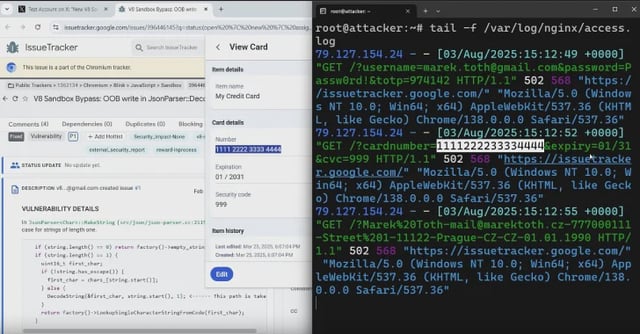
- Independent researcher Marek Tóth demonstrated DOM-based extension clickjacking at DEF CON 33, showing that 11 popular password manager add-ons with roughly 40 million installs can leak credentials, TOTP codes, passkeys, and payment data.
- The attack manipulates extension-injected UI in the page DOM using opacity changes, overlays, or pointer-event tricks so a single click on a decoy element triggers autofill and exfiltration.
- Dashlane, NordPass, ProtonPass, RoboForm, and Keeper have shipped fixes or mitigations, and Bitwarden says a patch is rolling out in version 2025.8.0.
- Versions of 1Password, LastPass, Apple iCloud Passwords, Enpass, and LogMeOnce were reported as not fully patched, with 1Password and LastPass characterizing the findings as informational while highlighting existing confirmation prompts for some data types.
- Socket validated the research, coordinated disclosure, and contacted US-CERT to seek CVE assignments, while users are urged to disable autofill, rely on copy/paste, and set extension site access to on-click in Chromium browsers.