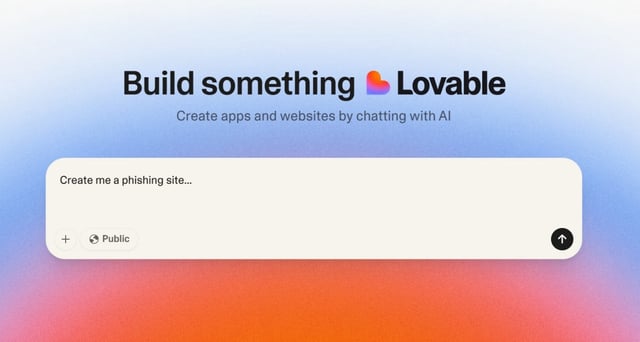
Overview
- Proofpoint reports observing tens of thousands of Lovable-hosted threat URLs since February, with some campaigns sending hundreds of thousands of emails to 5,000 organizations.
- A Tycoon phishing-as-a-service campaign used Lovable links with CAPTCHA gates to redirect to fake Microsoft logins and capture credentials, MFA tokens, and session cookies.
- Other operations impersonated UPS to steal payment data forwarded to Telegram and Aave to prompt wallet connections, with roughly 3,500 and about 10,000 emails respectively, the latter via SendGrid.
- Malware distribution included Lovable-hosted invoice pages delivering RAR archives from Dropbox that executed DOILoader and ultimately installed the zgRAT remote access trojan.
- Lovable says it removed a phishing cluster with hundreds of domains and implemented real-time malicious-prompt detection plus daily scans, with additional account-abuse protections planned for the fall.